TechSploits
- Making a trading Gameboy: A pocket exchange and algo trading platformquestdb.io Making a trading Gameboy: A pocket exchange and algo trading platform
An exchange and algo trading station in your pocket!

A nice in-depth post on the hardware too!
- Redbox HDDs are finding their way into the hands on individuals and they were not cleaned!digipres.club Foone🏳️⚧️ (@foone@digipres.club)
OH HEY BAD NEWS: when someone opens up the hard drive of a redbox unit, they can pull a file which has a complete list of titles ever rented, and the email addresses of the people who rented them, and where and when
> when someone opens up the hard drive of a redbox unit, they can pull a file which has a complete list of titles ever rented, and the email addresses of the people who rented them, and where and when
- Two never-before-seen tools, from same group, infect air-gapped devicesarstechnica.com Two never-before-seen tools, from same group, infect air-gapped devices
It’s hard enough creating one air-gap-jumping tool. GoldenJackal did it 2x in 5 years.

- 1 bug, $50,000+ in bounties, how Zendesk intentionally left a backdoor in hundreds of Fortune 500 companiesgist.github.com 1 bug, $50,000+ in bounties, how Zendesk intentionally left a backdoor in hundreds of Fortune 500 companies
1 bug, $50,000+ in bounties, how Zendesk intentionally left a backdoor in hundreds of Fortune 500 companies - zendesk.md

- gaining access to anyones browser without them even visiting a website - eva's sitekibty.town gaining access to anyones browser without them even visiting a website - eva's site
gaining access to anyones browser without them even visiting a website
What a good browser...
- 4 exploits, 1 bug: exploiting CVE-2024-20017 4 different waysblog.coffinsec.com 4 exploits, 1 bug: exploiting CVE-2024-20017 4 different ways
a post going over 4 exploits for CVE-2024-20017, a remotely exploitable buffer overflow in a component of the MediaTek MT7622 SDK.
- latchset/clevis: Automated Encryption Frameworkgithub.com GitHub - latchset/clevis: Automated Encryption Framework
Automated Encryption Framework. Contribute to latchset/clevis development by creating an account on GitHub.

to be paired with tang
- broadcast-box: A broadcast, in a box.github.com GitHub - Glimesh/broadcast-box: A broadcast, in a box.
A broadcast, in a box. . Contribute to Glimesh/broadcast-box development by creating an account on GitHub.

Not so much a sploit but an easy way to do broadcasting!
- Hacking a Virtual Power Plantrya.nc Hacking a Virtual Power Plant
I recently had solar panels and a battery storage system from GivEnergy installed at my house. A major selling point for me was that they have a local network API which can be used to monitor and…

- Tony Hawk's Pro Strcpyicode4.coffee Tony Hawk's Pro Strcpy
Tony Hawk's Pro Strcpy: A game save and RCE exploit for the Tony Hawk game series that can be used to hack Xbox, Playstation 2, Gamecube, and Xbox 360 consoles.

- [PDF] Cloudstrike Channel File 291 Incident Root Cause Analysis 08.06.2024
the "official" incident root cause analysis
- Secure Boot is completely broken on 200+ models from 5 big device makersarstechnica.com Secure Boot is completely broken on 200+ models from 5 big device makers
Keys were labeled "DO NOT TRUST." Nearly 500 device models use them anyway.

An article from July, but I bet you haven't updated your bios! Or you left it open on purpose?
- A Deep Dive into TPM-based BitLocker Drive Encryption – Sec Team Blog
A really good article on how TPMs work
- Technical Details on July 19, 2024 Outage | CrowdStrikewww.crowdstrike.com Technical Details on July 19, 2024 Outage | CrowdStrike
Learn more about the July 19, 2024 CrowdStrike outage and the technical details related to it.

The update that broke half of all enterprise servers. One of the official remediation steps is to "Reboot as many as 15 times"
Read more: https://community.intel.com/t5/Intel-vPro-Platform/Remediate-CrowdStrike-Falcon-update-issue-on-Windows-systems/m-p/1616593/thread-id/11795
- https://old.reddit.com/r/crowdstrike/comments/1e6vmkf/bsod_error_in_latest_crowdstrike_update/
- https://repost.aws/en/knowledge-center/ec2-instance-crowdstrike-agent
- https://azure.status.microsoft/en-gb/status
- regreSSHion: CVE-2024-6387
Update your openssh, now
- Hacking Millions of Modems (and Investigating Who Hacked My Modem)samcurry.net Hacking Millions of Modems (and Investigating Who Hacked My Modem)
Two years ago, something very strange happened to me while working from my home network. I was exploiting a blind XXE vulnerability that required an external HTTP server to smuggle out files, so I spun up an AWS box and ran a simple Python webserver to receive the traffic from the vulnerable server.

Unbelievable...
- Writing a Unix clone in about a month
Drew always has a hot take about a problem
- Brane Dump: How I Tripped Over the Debian Weak Keys Vulnerability
Recent HN Thread: https://news.ycombinator.com/item?id=39976225
- The xz sshd backdoor rabbithole goes quite a bit deeperthreadreaderapp.com Thread by @bl4sty on Thread Reader App
@bl4sty: the xz sshd backdoor rabbithole goes quite a bit deeper. I was just able to trigger some harder to reach functionality of the backdoor. there's still more to explore.. 1/n it requires sending a properly craf...…
The PoC thickens
- An IRC client in your motherboardaxleos.com An IRC client in your motherboard
I made a graphical IRC client that runs in UEFI. It’s written in Rust and leverages the GUI toolkit and TrueType renderer that I wrote for axle’s userspace. I was able to develop it thanks to the vmnet network backend that I implemented for QEMU. You can connect to an IRC server, chat and read messa...
UEFI IRC, the perfect companion to asking why your Linux boot partition no longer exists #joke
- xzbot: Notes, honeypot, and exploit demo for the xz backdoor (CVE-2024-3094)github.com GitHub - amlweems/xzbot: notes, honeypot, and exploit demo for the xz backdoor (CVE-2024-3094)
notes, honeypot, and exploit demo for the xz backdoor (CVE-2024-3094) - amlweems/xzbot
- Network tunneling with… QEMU?securelist.com Network tunneling with… QEMU?
While investigating an incident, we detected uncommon malicious activity inside one of the systems. We ran an analysis on the artifacts, only to find that the adversary had deployed and launched the QEMU hardware emulator.

- Cracking Meta’s Messenger Certificate Pinning on macOStexts.blog Cracking Meta’s Messenger Certificate Pinning on macOS
Bypassing certificate pinning in Meta’s Messenger application on macOS.
- World Server Throwing Championshipwww.cloudfest.com World Server Throwing Championship
The World Server Throwing Championship at CloudFest lets Cloud professionals demonstrate their raw power! Are you strong enough?

- Snake on a Switch [Video]
Video
Click to view this content.
Video link for those on clients who don't show links when they are videos: https://i.imgur.com/5jtvxPQ.mp4
- Ramrecovery: Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pigithub.com GitHub - anfractuosity/ramrecovery: Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pi. Loads many images of the Mona Lisa into RAM and recovers after powering off/on again.
Simple demo illustrating remanence of data in RAM (see Cold boot attack) using a Raspberry Pi. Loads many images of the Mona Lisa into RAM and recovers after powering off/on again. - GitHub - anfr...

Practical attacks with a Raspberry Pi.
- DEF CON 30 - Sam Bent - Tor - Darknet Opsec By a Veteran Darknet Vendor
YouTube Video
Click to view this content.
An interesting talk
- How I forked SteamOS for my living room PC
linux_gaming@lemmy.ml
- Interesting double-poly latches inside AMD's vintage LANCE Ethernet chipwww.righto.com Interesting double-poly latches inside AMD's vintage LANCE Ethernet chip
I've studied a lot of chips from the 1970s and 1980s, so I usually know what to expect. But an Ethernet chip from 1982 had something new: a ...

- Operation Triangulation: The last (hardware) mysterysecurelist.com Operation Triangulation: The last (hardware) mystery
Recent iPhone models have additional hardware-based security protection for sensitive regions of the kernel memory. We discovered that to bypass this hardware-based security protection, the attackers used another hardware feature of Apple-designed SoCs.

Pretty scary stuff in here
- [37C3] There oughta be a Game Boy capture cartridge.there.oughta.be There oughta be a Game Boy capture cartridge.
I present to you: The GB Interceptor. It is an adapter that goes between an unmodified Game Boy and the cartridge and offers a video stream of the game via USB. Click the image to see the video on youtube.com. The video above should give you a good overview of what it does, how it works and what its...
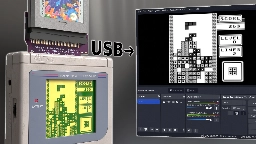
> https://github.com/Staacks/gbinterceptor
- [37C3] Full AACSess: Exposing and exploiting AACSv2 UHD DRM for your viewing pleasure (PDF)
Abstract
Intel’s Software Guard Extensions (SGX) promises an isolated execution environment, protected from all software running on the machine. As such, numerous works have sought to leverage SGX to provide confidentiality and integrity guarantees for code running in adversarial environments. In the past few years however, SGX has come under heavy fire, threatened by numerous hardware attacks. With Intel repeatedly patching SGX to regain security while consistently launching new (micro)architectures, it is increasingly difficult to track the applicability of various attacks techniques across the SGX design landscape. Thus, in this paper we set out to survey and categorize various SGX attacks, their applicability to different SGX architectures, as well as the information leaked by them. We then set out to explore the effectiveness of SGX’s update mechanisms in preventing attacks on real-world deployments. Here, we study two commercial SGX applications. First, we investigate the SECRET network, an SGX-backed blockchain aiming to provide privacy preserving smart contracts. Next, we also consider PowerDVD, a UHD Blu-Ray Digital Rights Management (DRM) software licensed to play discs on PCs. We show that in both cases vendors are unable to meet security goals originally envisioned for their products, presumably due to SGX’s long update timelines and the complexities of a manual update process. This in turn forces vendors into mak- ing difficult security/usability trade offs, resulting in security compromises.
-----
A worthwhile read for those who don't mind a more technical paper