This $70 device can spoof an Apple device and trick you into sharing your password
This $70 device can spoof an Apple device and trick you into sharing your password

A researcher built a $70 contraption designed to send pop-up prompts to nearby iPhones, which could trick targets into giving away their password.
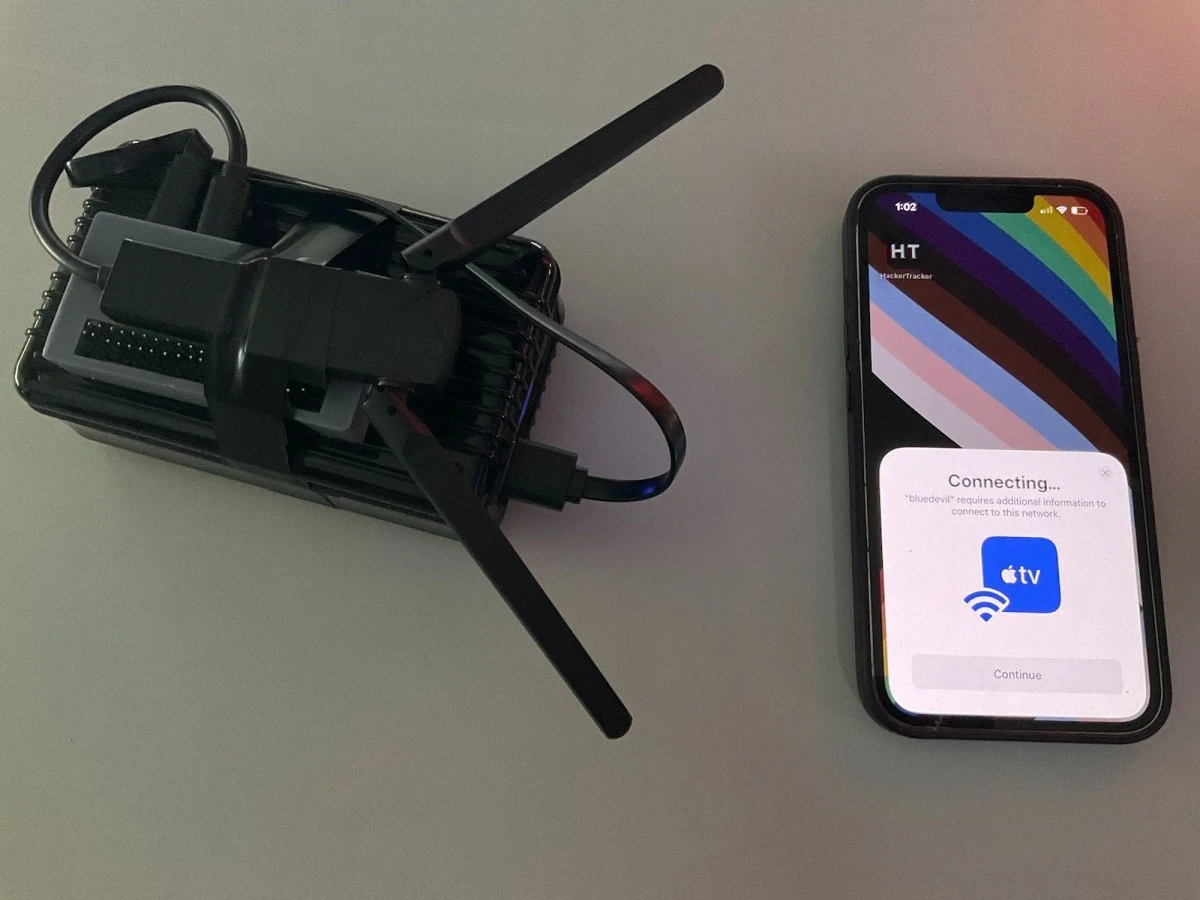
Attendees at Def Con, one of the world’s largest hacking conferences, are used to weird shenanigans, such as a seemingly innocuous wall of computer screens that display people’s passwords sniffed over the conference Wi-Fi network. But at this year’s event, even conference veterans were confused and concerned when their iPhones started showing pop-up messages prompting them to connect their Apple ID or share a password with a nearby Apple TV.
As it turned out, these alerts were part of a research project that had two goals.
One was to remind people that to switch off Bluetooth on an iPhone, you have to dig into the Settings app and not just tap it off on the quick-access Control Center, which is displayed by swiping down from the top right corner of the iPhone.
The other was “to have a laugh,” according to Jae Bochs, the security researcher who said they walked around the conference triggering these pop-ups with a custom-made device.
“I had it in my bag throughout linecon [an informal term that refers to the time spent in line at a conference], vendor areas, and when I was walking around. I tried to remember to disconnect it if I was hanging out for a talk,” Bochs said.
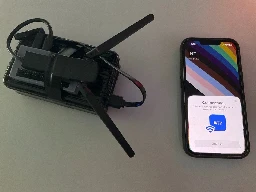
Bochs told TechCrunch that all they needed for this experiment was a contraption consisting of a Raspberry Pi Zero 2 W, two antennas, a Linux-compatible Bluetooth adapter, and a portable battery.
Bochs estimated that this combination of hardware, excluding the battery, costs around $70 and has a range of 50 feet, or 15 meters.
They explained that Apple’s protocols for Bluetooth low energy, or BLE, allow the company devices to communicate with each other. Bochs said that they focused on “proximity actions,” which appear on an iPhone screen when Apple devices are close to each other.
“Proximity is determined by BLE signal strength, and it seems most devices intentionally use lowered transmit power for these to keep the range short. I don’t :),” Bochs said.
Bochs also said they created a proof-of-concept that “builds a custom advertisement packet that mimics what Apple TV etc. are constantly emitting at low power,” effectively spoofing an Apple device that tries to repeatedly connect to nearby devices and triggers the pop-ups.
Unlike real Apple devices, his contraption wasn’t programmed to collect any data from nearby iPhones, even if the person tapped and accepted the prompts. But, in theory, they could have collected some data, according to Bochs.
“If a user were to interact with the prompts, and if the other end was set up to respond convincingly, I think you could get the ‘victim’ to transfer a password,” Bochs said. “There’s an issue known for a few years where you can retrieve phone number, Apple ID email, and current Wi-Fi network from the packets.”
The researcher said these issues are already known, at least since a 2019 academic paper that studied Apple’s Bluetooth low energy protocol and concluded that there are “several flaws” that “leak device and behavioral data to nearby listeners.”
“Individually, each flaw leaks a small amount of information, but in aggregate they can be used to identify and track devices over long periods of time,” the researchers wrote in the paper.
That’s why, Bochs said, they think Apple won’t do anything about this.
“Most or all of this is certainly by design, so that watches and headphones keep working with Bluetooth toggled,” they said.
Perhaps, they added, Apple could add a warning message when using the Control Panel toggles that alerts the user that tapping on its Bluetooth icon doesn’t completely shut off Bluetooth and their iPhone can still interact with proximity-activated beacons, such as Bochs’ contraption.
By turning Bluetooth off in the settings, an iPhone user would be safe from devices like theirs, Bochs explained.
Apple did not respond to a request for comment.